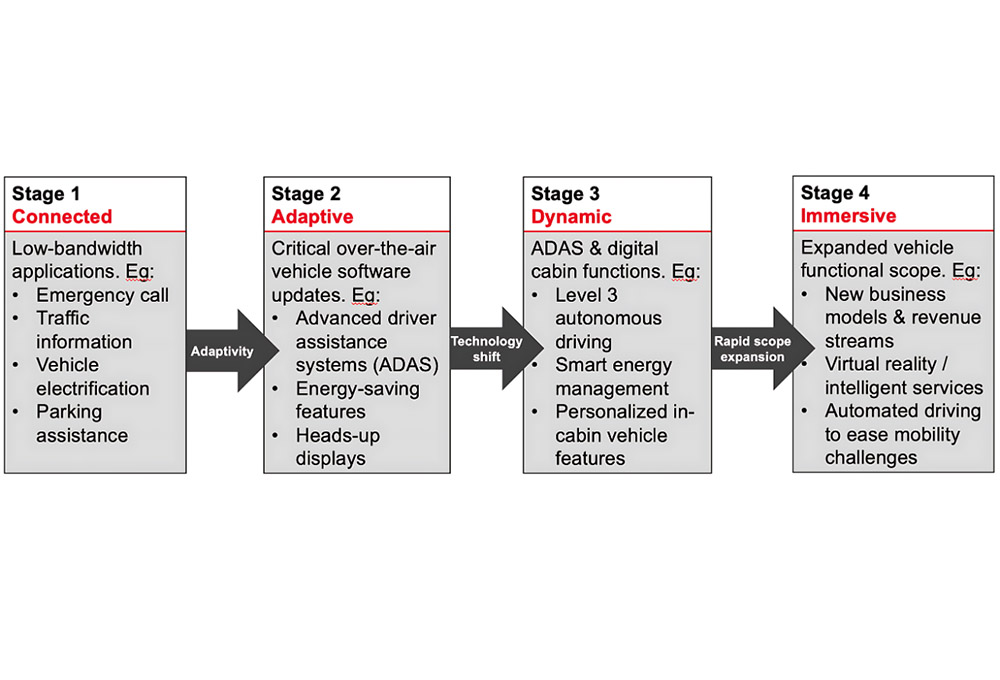
 主要由机械部件构成的传统汽车正在被日益普及的软件定义汽车(SDV)迅速取代,SDV不仅能让驾驶员和乘客与数字世界保持连接,还可通过自动驾驶功能让人们享受更安全、更轻松的旅程。
主要由机械部件构成的传统汽车正在被日益普及的软件定义汽车(SDV)迅速取代,SDV不仅能让驾驶员和乘客与数字世界保持连接,还可通过自动驾驶功能让人们享受更安全、更轻松的旅程。 更多的互联接口增加了软件定义车辆遭受网络攻击的可能性。(是德科技)
更多的互联接口增加了软件定义车辆遭受网络攻击的可能性。(是德科技) 汽车网络安全测试设备示例。(是德科技)
汽车网络安全测试设备示例。(是德科技)
软件定义汽车工程师可从物联网的发展中借鉴经验。
物联网的发展已向我们证明:互联程度的提升必将伴随着网络安全风险的增加。就在不久前,人们还对手机物联网的便捷性津津乐道,因为只需轻点屏幕就能够轻松享受银行服务和购买定制品牌等便利。然而,日益猖獗的网络犯罪令这种便利性大打折扣。据Statista统计,预计到2026年,网络犯罪活动将对全球经济造成超过每年20万亿美元的损失,较2022年增长了1.5倍。这些惊人的损失为我们敲响了警钟。因此,汽车行业正积极采取预防措施,以确保下一个移动大数据生态——SDV的安全性。
确保SDV的安全性极具挑战,因为互联程度的提升意味着潜在攻击的数量也会增加。网络黑客不仅使用了更先进的工具,而且攻击目标也不再局限于直接攻击私人汽车,而是包括车队、出行应用和各种服务。
|
|
|
|
|
||
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
为了管理这份冗长而详尽的测试清单,并满足审计追踪的要求,汽车制造商及其供应商正转而采用一站式的汽车网络安全测试解决方案。这些解决方案由电子系统和软件组成,可模拟受攻击车辆和黑客,通常包含以下关键要素:
-
无线和有线信号模拟器及分析仪,用于模拟和监控汽车的通信系统
-
侦察和漏洞利用服务器
-
应用和威胁情报库,可对其中不同的攻击活动进行筛选和规划
-
自动化和跟踪平台,用于管理测试数据和结果,以便进行报告和审查
本文由是德科技(Keysight Technologies)的行业和解决方案营销经理Hwee Yng Yeo撰写。
Old car models with mechanical components are rapidly giving way to the increasingly software-defined vehicle (SDV) with features that not only allow drivers and passengers to stay connected to the digital world but to enjoy a safer and easier journey with automated driving features (see Figure 1).
With increasing connectivity comes greater exposure to cybersecurity risks, as attested by the Internet of Things (IoT). It wasn’t so long ago when the conveniences of mobile connectivity seemed like a real boon, from banking and buying bespoke brands just a click away. That was until cybercrimes became a bane and a scourge, estimated to cost the global economy more than US $20 trillion a year by 2026, a 1.5x increase compared to 2022, according to Statista. These staggering dollar amounts represent hard lessons learned, and the automotive industry is stepping up on preemptive efforts to secure the next big data mine on wheels: the SDV.
Securing SDVs is extremely challenging, as increased connectivity means an increased number of potential attack interfaces (see Figure 2). Not only are cyber-hacking tools more advanced, but attackers are also moving beyond direct attacks against individual vehicles to target fleets, mobility applications, and services.
Evolving regulations and standards
Until the recent past, there were no global automotive cybersecurity standards, leaving automakers and their Tier 1 supply chain to develop their own cybersecurity testing requirements. In 2020, the United Nations’ World Forum for Harmonization of Vehicle Regulations (WP.29) introduced an automotive cybersecurity regulatory framework for OEMs.
For example, UN Regulation 155 (UN R155) mandates rigorous cybersecurity management system audits for automakers and their suppliers. It also requires automakers to obtain "vehicle type approval", which involves auditors conducting tests on vehicle products sharing the same electrical architecture. As recently as September 2021, SAE and the International Organization for Standardization (ISO) jointly published the ISO/SAE 21434 standard.
|
WP.29 regulations |
ISO/SAE 21434 standards |
|
UN R155 under WP.29 requires automakers to obtain a “certificate of compliance” under a cybersecurity management system (CSMS). This is to gain “vehicle type approval” so that the vehicle type can operate on public roads in participating nations.
UN R156 – mandates the deployment of a software update management system (SUMS) as a future condition of type approval.
Both regulations will be extended to existing architectures by July 2024. |
Cybersecurity engineering standard that implements a risk-driven CSMS focused on engineering vehicles securely.
The standard provides vocabulary, objectives, requirements, and guidelines as a foundation for common understanding throughout the supply chain.
This enables organizations to:
|
Automakers and their key suppliers must comply with UN R155 regulations while ISO/SAE 21434 is a set of guidelines. Both must go hand-in-hand if automakers want to bring new vehicle models to market.
Exactly how can automakers and Tier 1s translate both regulation and standards into action to secure the software-defined vehicle? The automotive industry has the benefit of leveraging learnings from cybersecurity experts who have been trying to stay ahead of hackers since the Internet of Things arrived. For example, the non-profit cybersecurity advocate group Open Web Application Security Project has an OWASP Top 10 list of vulnerabilities that automakers reference to secure the various attack interfaces of the software-defined vehicle. Table 2 shows the OWASP Top10 list, and the tests that automakers can implement for boosting automotive cybersecurity:
|
OWASP Top 10 list of preventable cybersecurity vulnerabilities |
||
|
|
Common threats |
Related tests |
|
1 |
Weak, guessable, or hardcoded passwords |
Brute force scanner |
|
2 |
Insecure network services |
Service discovery |
|
3 |
Insecure ecosystem interfaces |
Application layer scan and attack |
|
4 |
Lack of secure update mechanism |
Validation of secure communications |
|
5 |
Use of insecure or outdated components |
Vulnerability assessment |
|
6 |
Insufficient privacy protection |
Assess services access |
|
7 |
Insecure data transfer and storage |
Validation of secure communications |
|
8 |
Lack of device management |
Summarize device identification |
|
9 |
Insecure default settings |
Overall summary of device settings |
|
10 |
Lack of physical hardening |
You must lock your car! |
Putting security to the test
Testing is an essential part of the UN R155 automotive cybersecurity management system (CSMS). Different systems must be thoroughly tested, from onboard hardware like physical in-vehicle networks, electronic control units, and EV charging ports through all layers of the open systems interconnection (OSI) stack. Multiply that with different threat scenarios and design iterations, the list of tests is extensive.
To manage the exhaustive lists of tests and be able to manage and pass audit trails, automakers, and their suppliers are turning to turnkey automotive cybersecurity test solutions. These solutions comprise electronic systems and software to emulate a victim vehicle and hacker(s). They typically comprise these key elements (see Figure 3):
- Wireless and wireline signal emulators and analyzers to simulate and monitor the vehicle’s communication systems
- Reconnaissance and exploitive attack servers
- Application and threat intelligence library from which different attacks can be selected and scheduled
- Automation and tracking platform to manage test data and results for reporting and auditing
Early detection saves money – and reputation
Taking a page off the history of the Internet of Things, and in more recent times, the smartphone, where millions of dollars are lost daily to scammers and hackers, securing the connected smart vehicle of the future is both important and urgent. IoT and the smartphone changed the way we live. There is no going back to an off-grid world for most of us, despite the dangers of cyber exploitations.
SDVs will likely expand upon the connected way of living for us. Hopefully, with lessons learned on how to secure our connected world, automakers and their key suppliers can stay many steps ahead of cybercriminals waiting to exploit both individual car owners and organizations that run fleets and associated transportation systems and electric vehicle supply equipment. Rigorous testing throughout a vehicle’s life cycle will minimize the risks of automotive cyberattacks and help keep automakers and service providers off the headlines of who’s been hacked.
Hwee Yng Yeo is industry and solutions marketing manager at Keysight Technologies.
等级
打分
- 2分
- 4分
- 6分
- 8分
- 10分
平均分
